-
Featured services
Harness innovation to deliver value
Ensure short-term stability as you design a roadmap for new use cases in your industry with emerging technologies.
Explore Connected Industries -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Network as a Service
Popular Products
-
Private 5G
Our turnkey private 5G network enables custom-built solutions that are designed around unique use cases and strategies, and deployed, run and optimized through a full network-as-a-service model.
-
Managed Campus Networks
Our Managed Campus Networks services transform campus networks, corporate area networks and interconnected local area networks, and connect smart places and industries.
-
-
Services
Cloud Services
Popular Products
-
Cloud Migration and Transformation Services
Access the people, processes and technologies you need to deliver cloud migration projects that improve your return on investments.
-
Site Reliability Engineering Services
Get the most from your cloud investments when you harness our Site Reliability Engineering Services to support app development and lifecycle management.
-
-
Services
Edge as a Service
Client stories
-
Penske Entertainment and the NTT INDYCAR SERIES
Together with Penske Entertainment, we’re delivering digital innovations for their businesses – including INDYCAR, the sanctioning body of the NTT INDYCAR SERIES – and venues such as the iconic Indianapolis Motor Speedway, home to the Indianapolis 500.
-
Using private wireless networks to power IoT environments with Schneider Electric
Our combined capabilities enable a secure, end-to-end digital on-premises platform that supports different industries with the benefits of private 5G.
-
-
Services
Technology Solutions
Client stories
-
Services
Global Data Centers
-
Services
Digital Collaboration and CX

IDC MarketScape: Worldwide Datacenter Services 2023 Vendor Assessment
We provide a new kind of intelligent infrastructure to deliver better outcomes through technology.
Get the IDC MarketScape -
-
-
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-

Copilot for Microsoft 365
Everyone can work smarter with a powerful AI tool for everyday work.
Explore Copilot today -
-
Global Employee Experience Trends Report
Excel in EX with research based on interviews with over 1,400 decision-makers across the globe.
Get the EX report -
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-

NTT DATA and HEINEKEN
HEINEKEN revolutionizes employee experience and collaboration with a hybrid workplace model.
Read the HEINEKEN story -
- Careers
Topics in this article
Without some form of automation, larger scale infrastructure deployments, in particular, will struggle to maintain even the status quo in operational disciplines required today. A material number of incidents are related to poor systems hygiene through vulnerability, configuration, privilege and asset management. At a basic level, these operational requirements are ripe for automation and will help meet compliance obligations and reduce risk.
Starting the journey to automation
Defining a strategy to help shape your automation journey is critical to responding to rapid change and making way for digital transformation.
Below is an illustration of some different approaches to automation, depending on your risk profile, operational maturity and enterprise scale.
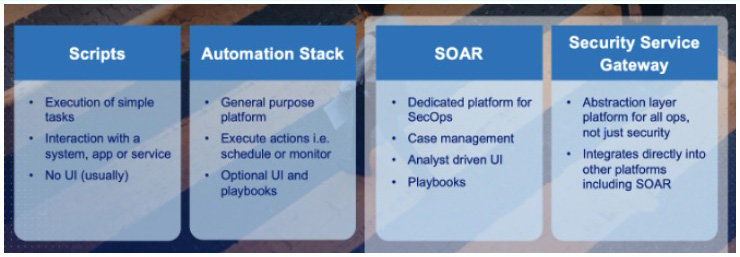
For many companies though, the journey begins with leveraging scripts as they are the foundation to build on further automation. Moving forwards into an automation stack will provide opportunities to automate mundane tasks; while not specific to security they may help streamline your operational objectives. This could involve scheduling regular audits across your infrastructure to patching systems.
Security Orchestration and Automation Response (SOAR) platforms combine multiple security processes and tools that assist with orchestration, automation, and response.
There is now significant interest in SOAR platforms, as they can automate once laborious tasks performed by security analysts to deliver faster response times and – as a result – can save you from a security breach.
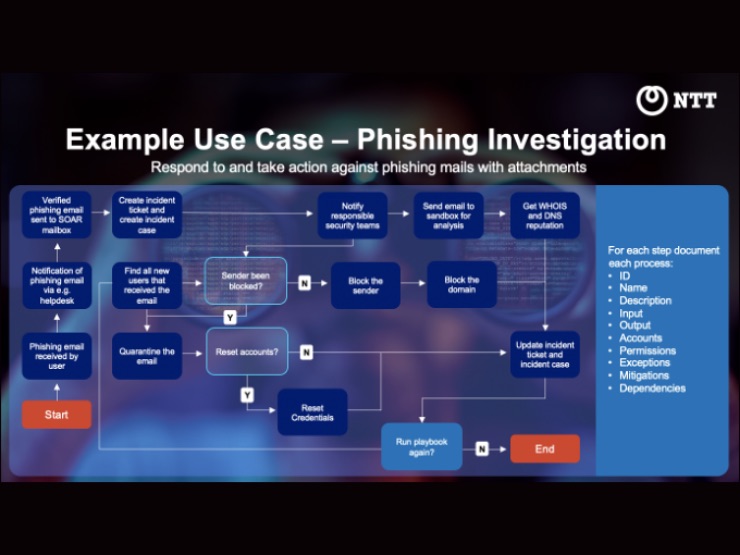
Take, for example, the use case of responding to an email incident, where potentially hundreds of malicious emails are sent to a company to harvest passwords through a fake login page hosted on a website. In the past, the task of identifying impacted users, blocking the domain, resetting passwords and removing email from mailboxes could take many hours. With automation, this task can be reduced to mere seconds or minutes.
Despite automation being a long-term commitment, the above examples are not mutually exclusive, and we can expect companies to employ multiple platform strategies to support the objectives of automation.
Evaluating your success
Success is a broad term but being able to evaluate how well your automation platform stacks up against your objectives using quantifiable metrics is vital to measure its effectiveness. Below are some strategies to evaluate and compare when using an automation platform versus performing the tasks manually:
- Lead time to enrich, triage, respond: How long did the case take the ingested alert to be enriched with contextual data e.g., domain reputation and determining asset ownership to establishing priority and risk to then responding through a block action?
- Keyboard stroke and mouse clicks: How streamlined is the process for the team logging cases, extracting necessary information and updating those service tickets? Count every keyboard stroke and mouse click and compare results.
- Rate of overall case closure: How long did it take to close the case end-to-end? Take into consideration when the alert was first known through to following your incident management process to closure.
Learning and reflecting as you go
SOAR use cases will be similar; but their implementation will be unique and based on your company’s requirements. As your company changes, analyst feedback is critical to success, requiring continuous engagement between your operations and SOC teams.
If there are any takeaways you should consider, begin by asking the following questions:
- Do your operational processes allow you to respond quickly enough?
- Where are you on your automation journey?
- Do you have a strategy that is endorsed by senior management to execute?

